Features
Manufacturing Intelligence Platform
Offering a full spectrum of Connect, Build, Analyze, Train, Optimise, Manage, Secure and Scale
How Klyff Works
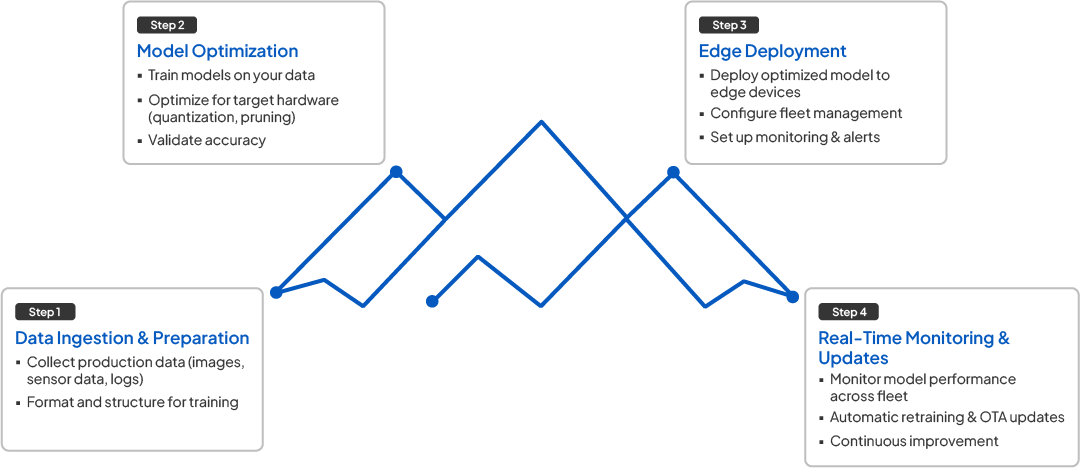
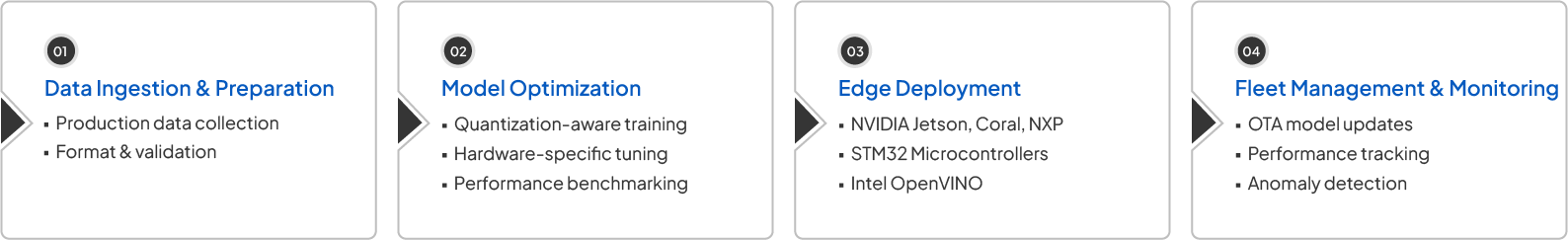
Advanced Model Optimization
TensorRT-powered quantization, pruning, and hardware-specific tuning. 50-70% model compression without accuracy loss.
- Quantization-Aware Training (QAT)
- Neural Architecture Search (NAS)
- Hardware profiling
- Performance benchmarking
Hardware Abstraction
Deploy on any edge device. NVIDIA, Google, Intel, ARM, STM32 — Klyff optimizes automatically.
- 8+ certified hardware platforms
- Automatic device detection
- Per-device optimization
- No vendor lock-in
Fleet Management
Manage 100+ edge devices from a single dashboard. OTA updates, monitoring, versioning, and rollback.
- Centralized dashboard
- Model versioning
- Automatic OTA updates
- Health monitoring
Privacy & Security
Data never leaves your factory. Edge-first design with federated learning support for multi-site deployments.
- Zero data exfiltration
- On-device processing
- Federated learning
- GDPR/HIPAA ready
Supported Hardware
Klyff is certified for NVIDIA Jetson, Google Coral, and Intel processors—on any device, from raw modules to complete industrial systems like Seeed Studio’s reComputer.
Integration
- Seeed reComputer J3011/J4012
- Seeed reComputer AI R2135
- Seeed reComputer R1025
- Arduino Opta, Arduino Rileva ME
- Infineon PSoC Edge
GPUs
- NVIDIA Jetson Orin Nano (275 TOPS, 5-25W)
- NVIDIA Jetson Orin (275 TOPS, 15-70W)
- NVIDIA Jetson AGX Thor (1035 INT8 TOPS, 40-130W)
Accelerators
- Google Coral Edge TPU (4 TOPS, 2W)
- Intel OpenVINO + Edge Processors
- NXP i.MX 8M Plus (2.3 TOPS, 5-15W)
Microcontrollers
- STM32H7 Series (sub-1W, TinyML)
- Qualcomm Dragonwing IQ (future roadmap)
Framework and Tools
Frameworks
- PyTorch
- TensorFlow
- Keras
- ONNX
- JAX
Optimization Engines
- TensorRT (NVIDIA)
- TFLite (Google)
- OpenVINO (Intel)
- ONNX Runtime
Deployment Tools
- Kubernetes
- Docker
- REST API
- gRPC
All the features
Connect
Device management
Secure orchestration of all interconnected devices
Seamlessly connect and manage a diverse set of devices. Collect asset data and deploy AI models on the devices
Easy Onboarding
Connect IoT devices and gateways including LoRa devices

Model Once, Reuse Always
Create a device template with default configurations and use it for all devices
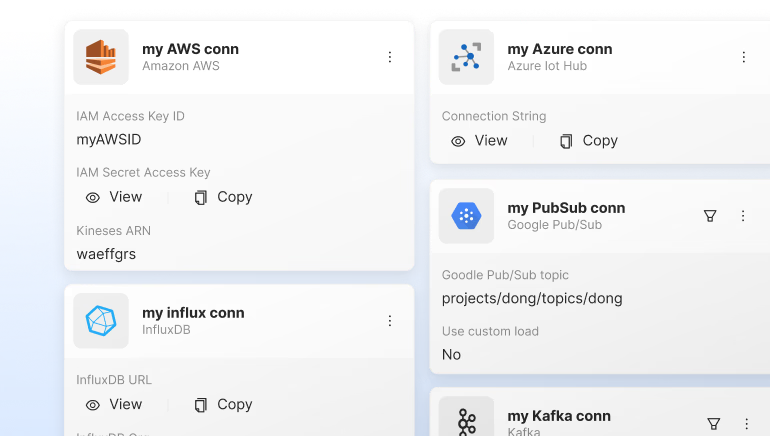
Tags & Custom fields
Arrange and manage devices efficiently with tags. Add custom attributes to devices

Connectivity integrations
Connect easily with plethora of internal and external systems

Replace, Upgrade & Re-register
Ripe and register old device with new without mapping change. Easy firmware upgrades over the air

Device simulator
No physical device at hand? No problem, our device simulator has got you covered!
Build
Data Flows
Process and React to Data with Rule Chains
Data Flows allow you to define your data path instantly and without coding. Transform and normalise data with drag and drop editor

Analyse
Dashboards
Impressive Real-time Dashboards
Rich IoT dashboards for data visualization and remote device control in real-time. More than 50 out-of-the-box widgets to support your use case

Train
Feature Engineering
State of the art Algorithms
Extract features from raw data and identify features relevant across your dataset to drive better decisions
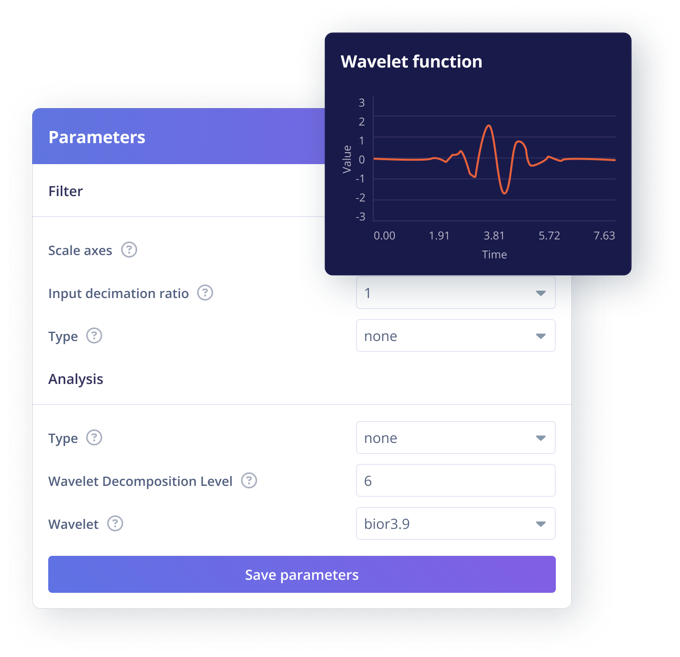
DSP Algorithms
Extract features from raw data and optimise for on-device inference performance
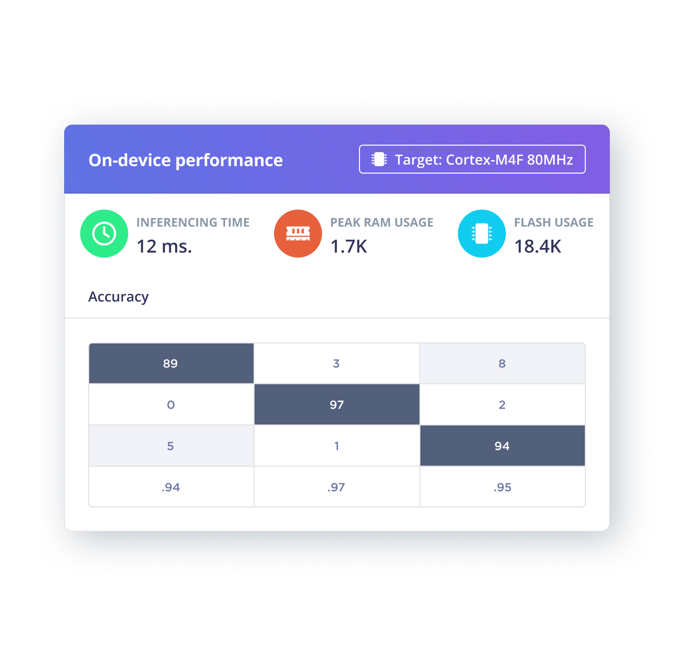
Profile on-device performance
Analyse impact of architectural decisions through real time on-device performance metrics
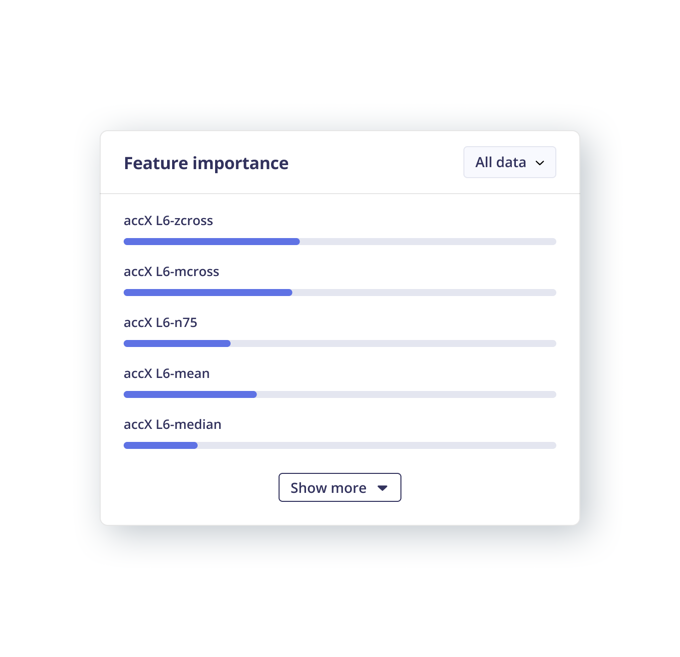
Feature Importance
Identify features most relevant across the data set for your use case
Optimise
Optimise on-device performance
Find a perfect balance between feature extraction algorithms and model architectures. Compare for Bandwidth, Latency, Economics, Reliability and Privacy (BLERP)

1. Reduce Memory Footprint
Supported by wide range of neural network kernels that allow to reduce the model's memory footprint by over 50%
2. Performance Calibration
Analyse False Activation Rate (FAR) and False Rejection Rate (FRR) on continuous real-world synthetic stream of data
3. Any device, no problem
Build the model once and deploy on any device. Klyff AI engine takes care of the optimisations
Manage
Track, monitor, authorise and restrict user access throughout the application’s life cycle from a single console. Role based access and control (RBAC). OAuth2 based authentication with support for different SSO sources.
Multi-tenant architecture out-of-the-box. Robustly manage multiple clients in a shared environment with isolated space for each client. Each tenant can have multiple clients, have multiple tenant administrators and support millions of devices

Create and manage alarms related to devices, assets, customers etc. Allows real-time monitoring and alarm propagation. Configure alarms for device disconnect or inactivity. Notify interested stakeholders with daily reporting and dashboards.

Rule Engine
Trigger actions based on data with easy drag & drop
Easy to use drag and drop rule chain designer. Process incoming device data with flexible rule chains based on entity attributes or message content. Forward data to external systems or trigger alarms using custom logic. Configure complex notification chains on alarms.

Secure
Security as a first class citizen
Practices implemented to safeguard the confidentiality, integrity, and accessibility of information generated and processed by the edge devices.
Robust encryption protocols. Protect sensitive information from origin to destination.
Adhere to stringent data protection and privacy standards like user consent, data minimization, and the rights to manage PII through GDPR.
Enable app owners to restrict and manage the amount of data accessible to users with access control features such as Profiles and Data Slicing.
Certified in ISO/IEC 27001, ISO/IEC 27701, ISO/IEC 27017, and ISO/IEC 27018, along with SOC 2 Type II compliance, ESQUEMA NACIONAL DE SEGURIDAD (ENS) requirements, and CSA STAR Self-Assessment.
Scale
Scalable and Resilient
Practices implemented to safeguard the confidentiality, integrity, and accessibility of information generated and processed by the edge devices.
Supported load increases linearly with servers added in clustering mode. No downtime or server restarts.
No master-worker relationship or hot standby. Automatic detection of failed nodes and replacement of failed nodes without downtime.
All persisted data is replicated in real-time using a reliable NoSQL database. SQL, NoSQL and Hybrid database options available
Dynamically expand the deployment of connected devices, while optimizing resources and enhancing connectivity.
Extensive integration support at the application, data and API level
Ready for your use case right from a few thousand messages per second to tens of millions per second